Background #
Device binding is a way to authenticate mobile application employees by ensuring that an app employee is in possession of a trusted device by having the device ID as a factor of authentication. This device binding capability offered by Cipher EIAM SDKs ensures that your mobile application is protected from mobile app impersonation fraud (i.e. even if a bad actor were to clone or reverse engineer your app, he/she will not be able to steal the information the secrets required for authenticating your mobile app employees)
What information can I bind using the “Device Binding” capability? #
Device Binding capability will help you to bind the following:
- Device ID - By default, we support “SIM Serial Number and Device ID” as the Device ID but you can easily be extended by raising an intake request
- Attributes - Additional information regarding the device - Hardware device information (e.g. IMEI/ESN, Mac address) Soft information (e.g. ANDROID_ID, UID) Service information (e.g. IMSI), etc. The example of the default attributes are as follows, you can easily be extended by raising an intake request
"metadata": {
"os": "ANDROID",
"appID": "XXX-android",
"hasNFC": "true",
"locale": "en_US",
"appName": "ABCapp",
"operators": "XXXX",
"osVersion": "",
"appVersion": "1.0",
"deviceType": "",
"macAddress": "02:00:00:00:00:00",
"buildNumber": "1",
"networkType": "WIFI",
"isWifiEnabled": "true",
"hasFrontCamera": "true",
"screenResolution": "2134x1080",
"isLocationEnabled": "true",
"authenticationType": "NONE",
"deviceManufacturer": "samsung"
}
Preconditions #
- A tenant created in Cipher EIAM. (You can request for a new tenant if you don’t have one.)
- You have access to the Authentication Center.
- You have your domain, sandbox and client already created
- You have setup the SDK
Step 1 - Setting up Auth Center #
Step 1.1: Go to your domain>Settings>People #
For example, your domain is “example.employee.com”
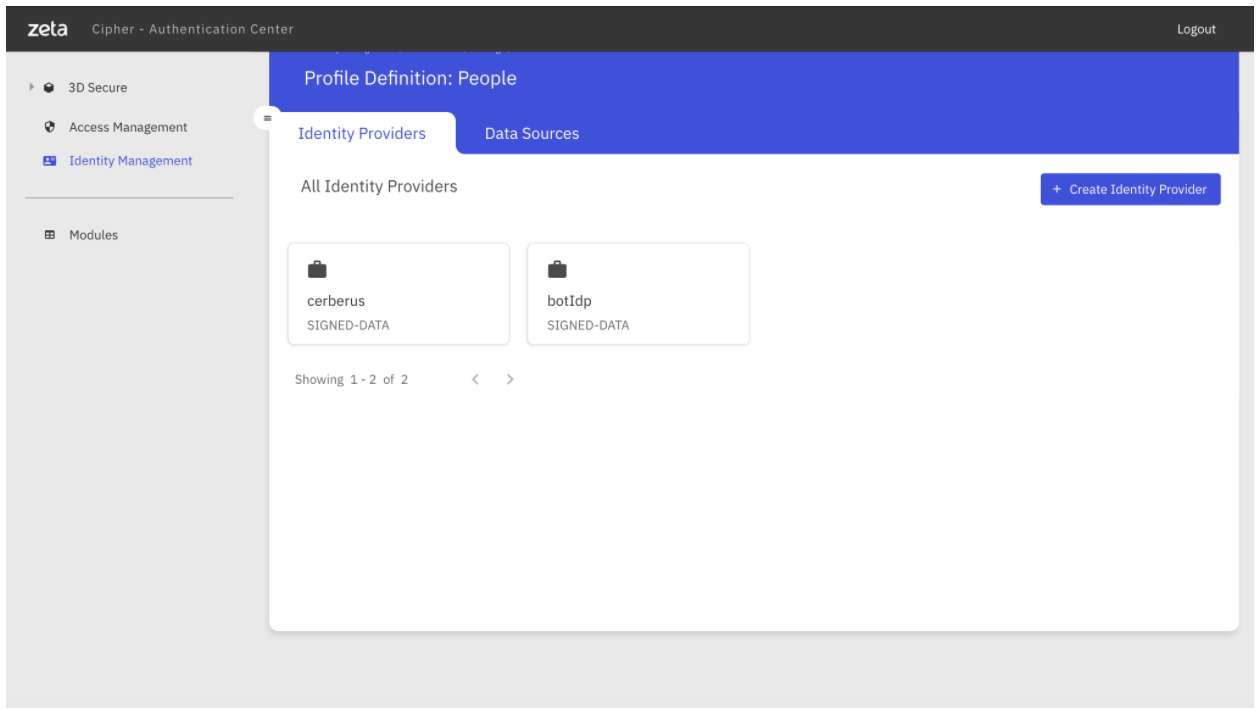
Here you can create the IDP for your device by clicking on “Create Identity Provider”
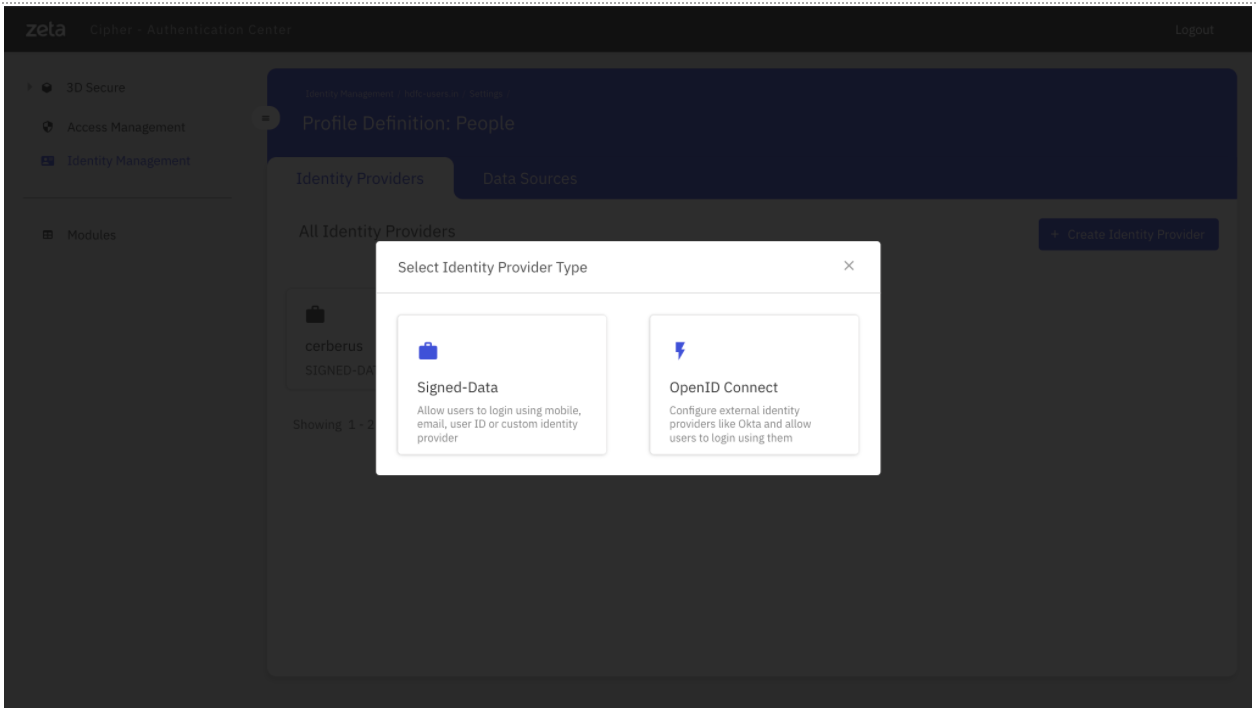
Step 1.2: Creating “Device Identity Type” for Device Binding #
- Click on “Signed Data”
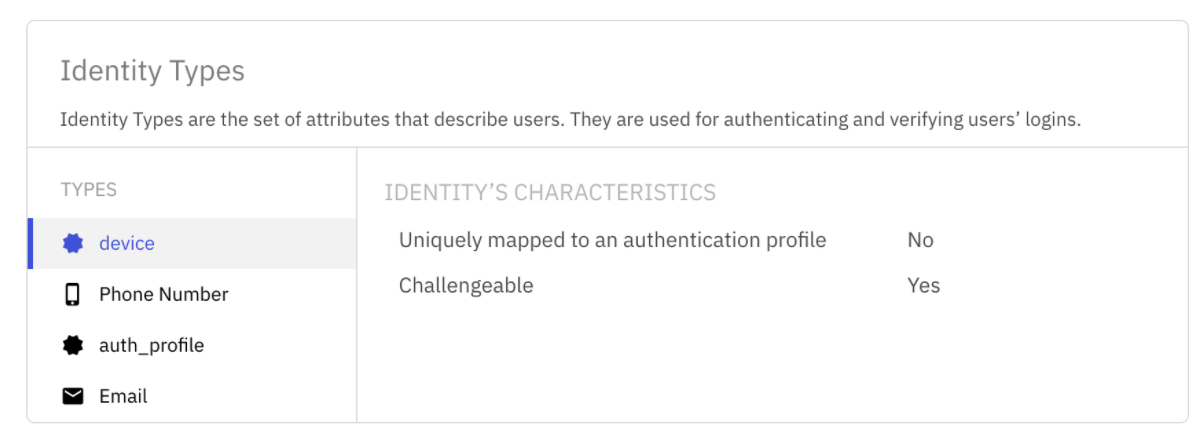
- Enter Basic Information, that is the name of the IDP
- Add the “device” Custom Identity Type. Please note, the Device has to be challengeable with public key as credential.
Step 1.3: Adding Credential Config to store the device public key #
You also have to add credential config so that the SDK can register the same on the server
curl --location --request PUT 'https://{{PP_Cipher_API}}/cerberus2/domains/<DomainID>/config/identities/auth_profile/credentialConfigs/public_key' \
--header 'Content-Type: application/json' \
--header 'Authorization: Bearer {{token}}' \
--data-raw '{}'
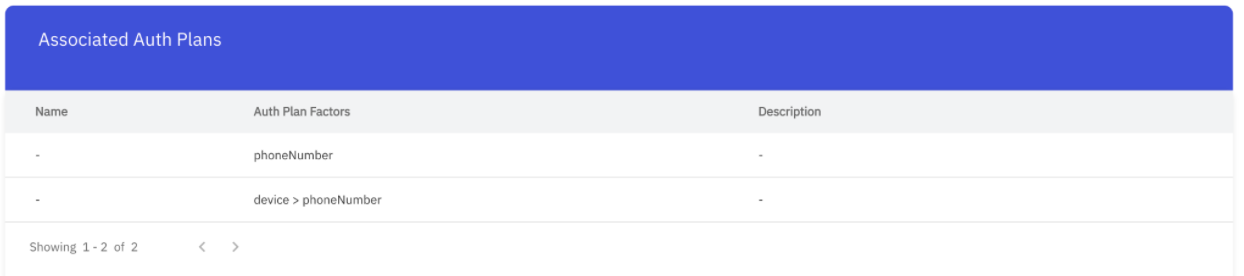
Step 1.4: Associate “device” to the SDK’s Auth Plan and “login” Scope #
Step 2 - Enabling Device Binding on the SDK #
- Have
"enableDeviceBinding": trueas on the cipher_sso json
cipher_sso JSON
{
"oauthTenantId": XXXX,
"zone": "U", // environment (prepro/staging/prod)
"enableDeviceBinding": true,
"authDataInSecuredStore": true //flag to stare private key from SSO & auth-token & refreshToken in secured (encrypted) store
}
- Then just trigger
/startSSOas per the setting up the SDK
Step 3 - Verify Device Binding #
In order to verify your device binding, i.e. whether the current device binding is the same as the previously generated device binding id, you must call the below method.
This will
/**
* Check if the current device binding is valid OR not. Currently, this check is based on the
* following logic.
*
* a) The current stored [DeviceBindingDetails] is not-null.
* b) The current stored [DeviceBindingDetails] is the same as the re-created details.
*
* @return Takes [IsDeviceBindingValidListener] as a listener param.
*/
fun isDeviceBindingValid(context: Context,
listener: IsDeviceBindingValidListener)
interface IsDeviceBindingValidListener: DeviceBindingFailureCallback {
fun done(isValid: Boolean)
}
Step 4 - Fetch device binding information of a employee #
You can do so by using the following API:
curl --location --request GET 'https://api.preprod.zeta.in/cerberus2/domains/abcbank-employees.in/auth_profiles/<Your Employee's Auth Profile ID' \
--header 'Authorization: Bearer {{Token}}'
Sample output
{
"domainId": "example.employee.com,
"authProfileId": "XXXXXXXXXXXX",
"name": "Angshu",
"identities": [
{
"identityId": 1,
"identityType": "phoneNumber",
"createdAt": 1629201444790,
"identityValue": "+91XXXXXXXX6",
"status": "ENABLED"
},
{
"identityId": 8,
"identityType": "device",
"createdAt": 1629364233048,
"identityValue": "e0b569166dcf8ef5:89918610400270796320",
"status": "ENABLED",
"metadata": {
"os": "ANDROID",
"appID": "1234-android",
"hasNFC": "true",
"locale": "en_US",
"appName": "UPI App",
"operators": "Airtel 4G",
"osVersion": "",
"appVersion": "1.0",
"deviceType": "",
"macAddress": "02:00:00:00:00:00",
"buildNumber": "1",
"networkType": "WIFI",
"isWifiEnabled": "true",
"hasFrontCamera": "true",
"screenResolution": "2134x1080",
"isLocationEnabled": "true",
"authenticationType": "NONE",
"deviceManufacturer": "ChinaPhoneHai"
}
}
],
"credentials": [
{
"identityType": "device",
"identityValue": "XXXXXXXXXXXXXXX:OOOOOOO10400270796320",
"credentialType": "public_key",
"identityId": 8,
"credentialId": "CCIIIAAASD_RCUKOMXCns_hIQ==",
"credentialValue": "XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX",
"metadata": {
"algorithm": "EC"
}
}
],
"isDirty": false,
"status": "ACTIVE",
"createdAt": 1629201444619,
"attributes": {},
"headers": {}
}


